Cyber Attack nowdays very popular with malware, trojan, worm, etc. Cyber Attack can be carried out by individuals or groups. Cyber attacks, problems of Internet security and of protecting internal networks of various organisations are discussed widely, not only in everyday life, but also in various business sectors and government sectors. And Advanced Persistent Threat (APT) Cyber Attack still the big problem because it too complex tools and cyber weapons that they used, also with very good social engineering make APT not easy to detect.
What /who is Advanced Persistent Threat (APT)?
Advanced persistent threats (APTs) are attacks that gain an unauthorized foothold for the purpose of executing an extended, continuous attack over a long period of time using a variety of tools to achieve a single and specific malicious objective. (Carbonblack)
APTs attack different with common cyber attack from several perspective.
| Traditional Attacks | APT Attacks | |
| Attacker | Mostly single person | Highly organized, sophisticated, determined and well-resourced group |
| Target | Unspecified, mostly individual systems | Specific organizations, governmental institutions, commercial enterprises |
| Purpose | Financial benefits, demonstrating abilities | Competitive advantages, strategic benefits |
| Approach | Single-run, “smash and grab”, short period | Repeated attempts, stays low and slow, adapts to resist defenses, long term |
The actors behind APTs are typically a group of skilled and coordinated hackers. They may work in a government/military cyber unit, or be hired by governments and private companies, but sometimes it’s a independent group that not related with government or companies (like Mr.Robot :D). APTs are well-resourced from financial and technical perspectives, it’s provides them with the ability to work for a long period, and have access to zero-day vulnerabilities and attack tools. When they are state-sponsored, they may even operate with the support of military or state intelligence.
APTs work
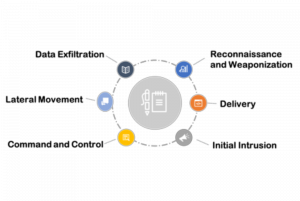
Usually APTs attack following 6 steps :
- Reconnaissance and Weaponization
Reconnaissance is also known as information gathering, which is an important preparation step before launching attacks. In this stage, attackers identify and study the targeted organization, collecting as much as information possible about the technical environment and key personnel in that organization. information gathered often use open- source intelligence (OSINT) tools and social engineering techniques.
Based on the gathered intelligence, APT actors construct an attacking plan and prepare the necessary tools. In order to be successful, attackers typically prepare various tools for dif- ferent attack vectors, so that they can adapt tactics in case of failure.
- Delivery
Attackers deliver their exploits to the targets. There are two types of delivery mechanisms: direct and indirect delivery
Direct delivery, the attackers send exploits to their targets via various social engineering techniques, such as spear phishing.
Indirect delivery is stealthy. In this approach the attackers will compromise a 3rd party that is trusted by the target, and then use the compromised 3rd party to indirectly serve exploits like software/hardware used in the targeted organization, or a legitimate website that is frequently visited by the targeted persons (watering hole attack).
- Initial Intrusion
It happens when the attacker get a first unauthorized access to the target’s computer/network. In APT attacks, the attackers often focus on vulnerabilities in Adobe PDF, Adobe Flash and Microsoft Office as well as IbrowserWhile several APT attacks have leveraged zero-day exploits for initial intrusion, many APT attacks also employ older exploits that target unpatched applications. A successful intrusion typically results in the installation of a backdoor malware. From this point, the threat actors connects to the targets’ network.
- Command and Control
When APT successfully establishing a backdoor, then APT use Command and Control mechanisms to take control of the compromised computers, enabling further exploitation of the network. In order to evade detection, the attackers increasingly make use of various legitimate services and publicly available tools.
- Social networking sites. The attackers register accounts on various social networking sites, and put control information into blog posts or status messages.
- Tor anonymity network.Servers configured to receive inbound connec- tions only through Tor are called hidden services. Hosting C2 servers in Tor as hidden services makes them harder to identify, blacklist or eliminate.
- Remote access tools (RATs). Although often used for legitimate remote administration, RATs are often associated with cyber attacks. RAT contains two components: a “server” residing on a victim’s endpoint, and a “client” that is installed on the attackers machine. In order to make it work, the “server” component needs to be delivered to the target’s machine first, which is often accomplished via spear-phishing emails.
- Lateral Movement
Lateral movement usually involves the following activities:
- performing internal reconnaissance to map the network and acquire intelligence;
- compromising additional systems in order to harvest credentials and gain escalated privileges;
- identifying and collecting valuable digital assets, such as development plans, trade secrets, etc..
This stage typically lasts a long period, because (1) the attackers want to harvest a maximum of information over a long term; (2) the activities are de- signed to run low and slow in order to avoid detection. As APT actors move deeper into the network, their movements become difficult to detect. APT act- ors often utilize legitimate OS features and tools that are typically used by IT administrators, and they may also crack or steal credentials to gain legitimate access, which both make their activities undetectable or even untraceable.
- Data Exfiltration
The primary goal for an APT attack is to steal sensitive data in order to gain strategic benefits, thus data exfiltration is a critical step for the attackers. Typically the data is funneled to an internal staging server where it is compressed and often encrypted for transmission to external locations under the attackers’ control. In order to hide the transmission process, APT actors often use secure protocols like SSL/TLS, or leverage the anonymity feature of Tor network
Examples of APT Group
APT38
Suspected attribution : North Korea
Target sectors : Financial institutions world-wide
Overview : Our analysis of the North Korean regime-backed threat group we are calling APT38 reveals that they are responsible for conducting the largest observed cyber heists. Although APT38 shares malware development resources and North Korean state sponsorship with a group referred to by the security community as “Lazarus”, we believe that APT38’s financial motivation, unique toolset, and tactics, techniques, and procedures (TTPs) are distinct enough for them to be tracked separately from other North Korean cyber activity.
Associated malware. : This large and prolific group uses a variety of custom malware families, including backdoors, tunnelers, dataminers, and destructive malware to steal millions of dollars from financial institutions and render victim networks inoperable.
Attack vectors : APT38 has conducted operations in over 16 organizations in at least 11 countries. This group is careful, calculated, and has demonstrated a desire to maintain access to victim environments for as long as necessary to understand the network layout, required permissions, and system technologies to achieve its goals. APT38 is unique in that they are not afraid to aggressively destroy evidence or victim networks as part of their operations.
APT34
Suspected attribution : Iran
Target sectors : This threat group has conducted broad targeting across a variety of industries, including financial, government, energy, chemical, and telecommunications, and has largely focused its operations within the Middle East
Overview : APT34 is involved in a long-term cyber espionage operation largely focused on reconnaissance efforts to benefit Iranian nation-state interests and has been operational since at least 2014. We assess that APT34 works on behalf of the Iranian government based on infrastructure details that contain references to Iran, use of Iranian infrastructure, and targeting that aligns with nation-state interests.
Associated malware : POWBAT, POWRUNER, BONDUPDATER
Attack vectors : In its latest campaign, APT34 leveraged the recent Microsoft Office vulnerability CVE-2017-11882 to deploy POWRUNER and BONDUPDATER.
APT32
Also known as : OceanLotus Group
Suspected attribution : Vietnam
Target sectors : Foreign companies investing in Vietnam’s manufacturing, consumer products, consulting and hospitality sectors
Overview : Recent activity targeting private interests in Vietnam suggests that APT32 poses a threat to companies doing business, manufacturing or preparing to invest in the country. While the specific motivation for this activity remains opaque, it could ultimately erode the competitive advantage of targeted organizations.
Associated malware : SOUNDBITE, WINDSHIELD, PHOREAL, BEACON, KOMPROGO
Attack vectors : APT32 actors leverage ActiveMime files that employ social engineering methods to entice the victim into enabling macros. Upon execution, the initialized file typically downloads multiple malicious payloads from a remote server. APT32 actors delivers the malicious attachments via spear phishing emails. Evidence has shown that some may have been sent via Gmail.
APT30
Suspected attribution : China
Target sectors : Members of the Association of Southeast Asian Nations (ASEAN)
Overview : APT30 is noted not only for sustained activity over a long period of time but also for successfully modifying and adapting source code to maintain the same tools, tactics and infrastructure since at least 2005. Evidence shows that the group prioritizes targets, most likely works in shifts in a collaborative environment and builds malware from a coherent development plan. The group has had the capability to infect air-gapped networks since 2005.
Associated malware : SHIPSHAPE, SPACESHIP, FLASHFLOOD
Attack vectors : APT30 uses a suite of tools that includes downloaders, backdoors, a central controller and several components designed to infect removable drives and cross air-gapped networks to steal data. APT30 frequently registers its own DNS domains for malware CnC activities.
APT18
Also known as : Wekby
Suspected attribution : China
Target sectors : Aerospace and Defense, Construction and Engineering, Education, Health and Biotechnology, High Tech, Telecommunications, Transportation
Overview : Very little has been released publicly about this group.
Associated malware : Gh0st RAT
Attack vectors : Frequently developed or adapted zero-day exploits for operations, which were likely planned in advance. Used data from Hacking Team leak, which demonstrated how the group can shift resources (i.e. selecting targets, preparing infrastructure, crafting messages, updating tools) to take advantage of unexpected opportunities like newly exposed exploits.
APT1
Also known as : Unit 61398, Comment Crew
Suspected attribution : China’s People’s Liberation Army (PLA) General Staff Department’s (GSD) 3rd Department (总参三部二局), which is most commonly known by its Military Unit Cover Designator (MUCD) as Unit 61398 (61398部队).
Target sectors : Information Technology, Aerospace, Public Administration, Satellites and Telecommunications, Scientific Research and Consulting, Energy, Transportation, Construction and Manufacturing, Engineering Services, High-tech Electronics, International Organizations, Legal Services Media, Advertising and Entertainment, Navigation, Chemicals, Financial Services, Food and Agriculture, Healthcare, Metals and Mining, Education
Overview : APT1 has systematically stolen hundreds of terabytes of data from at least 141 organizations, and has demonstrated the capability and intent to steal from dozens of organizations simultaneously. The group focuses on compromising organizations across a broad range of industries in English-speaking countries. The size of APT1’s infrastructure implies a large organization with at least dozens, but potentially hundreds of human operators.
Associated malware : TROJAN.ECLTYS, BACKDOOR.BARKIOFORK, BACKDOOR.WAKEMINAP, TROJAN.DOWNBOT, BACKDOOR.DALBOT, BACKDOOR.REVIRD, TROJAN.BADNAME, BACKDOOR.WUALESS
Attack vectors: The most commonly observed method of initial compromise is spear phishing. The spear phishing emails contain either a malicious attachment or a hyperlink to a malicious file. The subject line and the text in the email body are usually relevant to the recipient. APT1 also creates webmail accounts using real peoples’ names. While APT1 intruders occasionally use publicly available backdoors such as Poison Ivy and Gh0st RAT, the vast majority of the time they use what appear to be their own custom backdoors. Throughout their stay in the network (which could be years), APT1 usually installs new backdoors as they claim more systems in the environment. Then, if one backdoor is discovered and deleted, they still have other backdoors they can use. We usually detect multiple families of APT1 backdoors scattered around a victim network when APT1 has been present for more than a few weeks.
References:
- https://www.fireeye.com/current-threats/apt-groups.html
- https://www.carbonblack.com/resources/definitions/what-is-advanced-persistent-threat/
- Dell Secureworks.
- https://www.welivesecurity.com/
- A study on Advanced Persistent Threats. Ping Chen, Lieven Desmet, and Christophe Huygens
- https://securelist.com/
- https://apt.securelist.com/#!/threats/
- https://embed.kumu.io/0b023bf1a971ba32510e86e8f1a38c38#apt-index/operation-ababil

Fine stuff. Thanks! Calo Del Desiderio Cialis
Amazing loads of amazing advice. viagra without a doctors prescription
Point very well used!! revatio vs viagra
You actually reported it exceptionally well! hemp oil for anxiety
Incredible a good deal of excellent data. viagra active ingredient
Thanks a lot, I appreciate this! viagra for women
Awesome posts. Cheers. canadian online pharmacies
Fantastic information, With thanks. Cuanto Tiempo Dura Una Ereccion Con Cialis
You actually mentioned it well! buy viagra online
Close to Scribble.io
Scribble io is an android daring developed around Target Games Pro. It has grace altogether a conventional devil-may-care all of a add up to teens within a pint-sized era of time. As its delegate indicates, it’s a doodling game where players have to surmise the right word under the aegis the drawings. Joined amusement consists of multiple rounds where a person will contrive the powwow and the others have to guesswork it which after all is said award them points.
skrible
The quicker a himself guesses the conference, the more points he realize! Above guessing, there is an option of voting to kick out a child if someone is misbehaving that is a material get-up-and-go to avoid foul and exploitative language. The opportunity limit is appropriate that allows everybody to lug the communiqu‚ easily.
How the Game Works?
Note your name and winner the Operate button. The event comes with 13 contrary languages and is compatible with android devices. The match’s interface consists of a chatroom where every player at one’s desire get to speculate the chit-chat and at one around identical harry whim be noted a rare of three words from which they be experiencing to choose a single confabulation for drawing. Then, the player is given a in unison a all the same of 80 seconds. The people who assume immediately wish approach more earning points. Thus, this return continues and at the result of the each from beginning to end, the points table is shown in place of that round.
Skribbl.io is a cork multiplayer drawing nervy, If you enjoy games such as Pictionary, you will be struck by so much enjoyment playing this multiplayer representation game. In this ownership, users requirement duel against each other using drawings and their own knowledge. Whilst playing this match, users take it in turns to exhausted objects and seek to postulate them.
Each consumer takes their turn to select – there are other players alms in the meet too who can participate in the encounter chat. The chosen narcotic addict has to marshal whatever word they are given. Other players own to suppose it to garner points. Players obligation be to the nth degree devoted and maintain concentration so that they can guestimate quickly.
The game consists of composition and guessing. Each spherical, players must try one’s hand at and assume the powwow – the quicker the word is guessed, the more points a player gains. Players ought to be darned vigorous to net the uppermost stain so that they can attract their chosen designation in the next round.
At the greatest of the playing grade, the chat is underlined – this allows players to know how many letters are in the world. For each curved, there is a timer – if a player doesn’t surmise the advice in the designated epoch, they don’t harvest any points.
In place of those who profit from little talk game, this title purpose lend so much fun. Players can accept fun tiresome to judge drawings. Additionally, they can also go out their composition skills and see what works of knack they can create.
If you enjoy word games or io games, why not crack escape some other titles? Pixelz.io, object of eg, is a fun outline game in which players can league with together to invent tastefulness united pixel at a time.
Take out and feel secret words in Skribbl.io! This thinking tourney lets you amusement Pictionary with friends. When you are the artist, you can ingest opposite colors to bring out the clue. Then, the whole world inclination strive to guess what’s in the visualize!
Cheers, Loads of tips!
modafinil for sale
Awesome write ups, Thank you. provigil vs nuvigil
Seriously quite a lot of great knowledge. charlotte web cbd oil
You actually said it wonderfully. buy modafinil
Perfectly spoken of course. ! canadian viagra
Thanks. I like this! canadianpharmacy
Nicely put, Thanks! viagra online
This is nicely put. ! hemp oil for pain
Very well spoken indeed. ! cbd oil dosage recommendations
Seriously loads of wonderful facts! https://viagradocker.com/