Kopiluwak, Fancy Bear, Cozy Bear?
What is on your mind if you hear those words?
Those words contain something about coffee, cute animal and far away from something dangerous. But in security world those words have big concern because it related with APT attack, especially related with APT28 and APT29. On 2016 Fancy Bear and Cozy Bear so famous in cyber world, because they are indicated with cyber attack during US election.
Can cyber attack group interfere elections process?
Since 2007 APT28 active but received public attention during 2016 when it was indicated in series of cyber attack to the US presidential election. APT28 and APT29 indicated actors behind the cyber attacks targeted government organizations, think tanks, universities, and corporations. APT29 entered into the party systems in summer 2015 and APT28 entered in spring 2016.
In summer 2015, APT29 spearphishing campaign directed emails contain malicious link to over 1,000 recipients, including U.S. Government victioms. APT29 success send spearphising email and host malware, the results are they are compromised a U.S. political party. At least one targeted individual activated links to malware hosted on operational infrastructure of opened attachments containing malware. APT29 delivered malware to the political party’s systems, established persistence, escalated privileges, enumerated active directory accounts, and exfiltrated email from several accounts through encrypted connections back through operational infrastructure.
In spring 2016, APT28 do same spearphising campaign, but this time they are tricked recipients into changing their passwords throught fake webmail domain hosted on APT28 infrastructure. With the credential, APT28 was able to gain access and steal informations from systems. And because APT28 and APT29 attack during election and leak cresidential data on U.S election it was interfere or influence the democratic process.
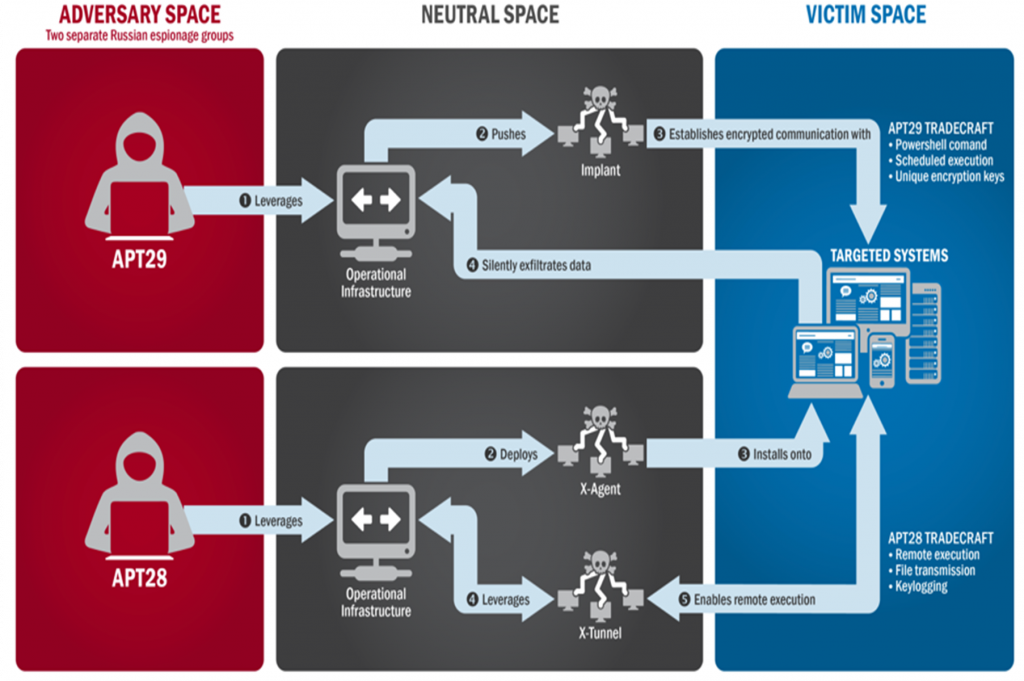
Figure 1. APT28 and APT29 attack process on US election. (source: GRIZZLY STEPPE – Russian Malicious Cyber Activity)
In 2016 also Taiwan election was reported that the election was going to be the target of a series of attacks by Chinese threat actors. Attacker use ofiice documents like .doc, .docs, .xls and pdf ,that contain macros and executable program when office documents was click opened. And then program behind the document (malware, backdoor, etc) will active without notification.
On 2015 the APT28 group stole 16 gigabytes of data from the German parliament. The hackers used a malware to gain access the internal servers of the Bundestag. This attack was indicated for preparing attck election process on Germany.
On 2017, Denmark reported a cyber intrusion in several Defense Ministry. According to the report, hackers belonging to the notorious APT28, were behind the attack that was part of an ongoing cyber espionage campaign that targeted the Danish Defense Ministry.
And also in 2017, APT28 group launched spearphishing against the campaign of the French Presidential candidate Emmanuel Macron. The APT28 attacks against the Emmanuel Macron staff used replicas of legitimate URLs and exploited the attack technique dubbed.
On 2018, Cambodia election process also targeted by cyber attack. Chinese APT effortsrelated with this attack use spearphising with office document. Chinese APT base on FireEye analysis identified new tools, EVILTECH and DADBOD.
Range of cyber attack in Election process
- DEFACEMENT
Defacement describes the illegal modification of online content. Defacement is a type of attack often carried out as part of a politically motivated attack to spread propaganda. Taking into account that election commissions, as well as political parties and interest groups, use online channels to communicate with the public, this underlines the potential for future attacks.
- DENIAL-OF-SERVICE ATTACKS
In some ways comparable to the defacement of websites are Denial-of-Service (DoS) attacks that are aiming to make websites or services unavailable. Typical targets within the context of elections are websites of election commissions, political parties and candidates.
- ESPIONAGE/DATA EXFILTRATION
Two of the most widely publically discussed attacks within the US presidential election 2016 were related to the alleged exfiltration of data. It was reported that offenders were able to obtain data (e-mails) both from computer systems of the Democratic Nation Convention.
- PUBLICATION OF OBTAINED INFORMATION
Both in the reported attacks in the 2016 US presidential election and in the 2017 French election, the mere fact that offenders obtained access to e-mails was not seen as the greatest damage, it was the fact that those e-mails were published and make some debates about election process.
- ATTACKS AGAINST ELECTION SERVER
Election server have some crucial data that can make chaos election process, because it source of all election data. If election process not use voter machine and still use conventional methode (use paper), attacking election server can be most target because it contain some data like : result, voter data, region raw data, etc. Some methods attack usually :
- Injection Flaws are broad web application attack techniques that attempt to send commands to a browser, database, or other system, allowing a regular user to control behavior. The most common example is SQL injection, which subverts the relationship between a webpage and its supporting database, typically to obtain information contained inside the database. Another form is command injection, where an untrusted user is able to send commands to operating systems supporting a web application or database.
- Cross-site scripting (XSS) vulnerabilities allow threat actors to insert and execute unauthorized code in web applications. Successful XSS attacks on websites can provide the attacker unauthorized access.
- Server vulnerabilities may be exploited to allow unauthorized access to sensitive information. An attack against a poorly configured server may allow an adversary access to critical information including any websites or databases hosted on the server.
- MISLEADING INFORMATION
Both the US election and France election, whose computer systems were reported to have been hacked and internal e-mails published, have indicated that some published e-mails were manipulated to mislead the public. Mixing authentic and manipulated documents could be a strategy to maximise the negative impact of such an attack. This was not the only incident where “misleading” or “fake” news played a role.
RECOMMENDED MITIGATION
- Patch applications and operating systems – Vulnerable applications and operating systems are the targets of most attacks. Ensuring these are patched with the latest updates greatly reduces the number of exploitable entry points available to an attacker. Use best practices when updating software and patches by only downloading updates from authenticated vendor sites.
- Application whitelisting – Whitelisting is one of the best security strategies because it allows only specified programs to run while blocking all others, including malicious software.
- Restrict administrative privileges – Threat actors are increasingly focused on gaining control of legitimate credentials, especially those associated with highly privileged accounts. Reduce privileges to only those needed for a user’s duties. Separate administrators into privilege tiers with limited access to other tiers.
- Network Segmentation and Segregation into Security Zones – Segment networks into logical enclaves and restrict host-to-host communications paths. This helps protect sensitive information and critical services and limits damage from network perimeter breaches.
- Input validation – Input validation is a method of sanitizing untrusted user input provided by users of a web application, and may prevent many types of web application security flaws, such as SQLi, XSS, and command injection.
- File Reputation – Tune Anti-Virus file reputation systems to the most aggressive setting possible; some products can limit execution to only the highest reputation files, stopping a wide range of untrustworthy code from gaining control.
- Understanding firewalls – When anyone or anything can access your network at any time, your network is more susceptible to being attacked. Firewalls can be configured to block data from certain locations (IP whitelisting) or applications while allowing relevant and necessary data through.
Refrences :
- INTERNET ORGANISED CRIME THREAT ASSESSMENT (IOCTA) 2017 (EUROPOL)
- GRIZZLY STEPPE – Russian Malicious Cyber Activity (Joint Analysis Report DHS and FBI)
- SENATE INTELLIGENCE COMMITTEE: RUSSIA AND 2016 ELECTION (FireEye)
- https://www.volexity.com/blog/2016/11/09/powerduke-post-election-spear-phishing-campaigns-targeting-think-tanks-and-ngos/
- https://www.crowdstrike.com/blog/bears-midst-intrusion-democratic-national-committee/
- https://www.symantec.com/blogs/election-security/apt28-espionage-military-government
- https://pwc.blogs.com/cyber_security_updates/
- https://www.proofpoint.com/us/threat-insight/post/turla-apt-actor-refreshes-kopiluwak-javascript-backdoor-use-g20-themed-attack
- https://resources.infosecinstitute.com/
- http://securityaffairs.co/wordpress/58361/apt/emmanuel-macron-apt28.html
- https://www.fireeye.com/blog/threat-research/2018/07/chinese-espionage-group-targets-cambodia-ahead-of-elections.html
- https://unit42.paloaltonetworks.com/evilgrab-delivered-by-watering-hole-attack-on-president-of-myanmars-website/

This is actually beneficial facts my friend. you are a exceptionally most luxurious writer . i lust after to portion with you my website as well. foresee me what do you think approximately it
[url=https://medium.com/@motivoscem/where-to-buy-youtube-views-and-why-buy-cheap-youtube-views-89007d6035dd]https://medium.com/@motivoscem/where-to-buy-youtube-views-and-why-buy-cheap-youtube-views-89007d6035dd[/url]
really nice
This is definitely credible tidings my friend. you are a exceptionally most luxurious scribe . i lust after to dividend with you my website as well. tell me what do you believe approximately it
[url=https://tinyurl.com/smj3gl9]buy youtube views[/url]
Thankyou again for posting such good content. Cheers
This is a awfully good post. Thankyou an eye to keeping us informed.
[url=http://forextrend.club]what is forex[/url]
I could not resist commenting. Perfectly written!
CYBER ATTACKS ON ELECTION PROCESS – Pentesting.id http://prediksitogeljitu.co
sonic the hedgehog coloring pages american girl coloring pages planets coloring pages november coloring pages toothless coloring pages police coloring pages incredibles 2 coloring pages alien coloring pages num noms coloring pages jungle coloring pages zootopia coloring pages
Very nice write-up. I definitely appreciate this website.
Keep it up!
Today, I went to the beach front with my kids.
I found a sea shell and gave it to my 4 year old daughter and said “You can hear the ocean if you put this to your ear.” She put the shell
to her ear and screamed. There was a hermit crab inside and it pinched her ear.
She never wants to go back! LoL I know this is entirely off topic but I had to
tell someone!
Hurrah, that’s what I was searching for, what a data! existing here at this webpage, thanks admin of this site.
I don’t even know the way I ended up here, but I believed this submit was good.
I don’t recognize who you’re however certainly you are going to a famous blogger when you
aren’t already. Cheers!
Wonderful blog! I found it while searching on Yahoo News.
Do you have any tips on how to get listed in Yahoo News? I’ve been trying for a while but I never seem to get there!
Cheers
Fantastic post however , I was wanting to know if you could write
a litte more on this topic? I’d be very grateful if you
could elaborate a little bit further. Cheers!
Thanks a bunch for sharing this with all folks you actually
understand what you are talking about! Bookmarked. Please
additionally seek advice from my website =). We can have a link
alternate agreement among us
This is a very exciting post. Shroud them coming.
Behold my website here: [url=http://motionsingle6.edublogs.org]xbody[/url]
This is a dialect right spellbinding post. Smother them coming.
Discern my website here: [url=https://securesingle8.soup.io]xbody[/url]
This is a dialect right spellbinding post. Put them coming.
Discern my website here: [url=http://secureface4.pen.io]xbody[/url]
This is a surely interesting post. Put them coming.
Discern my website here: [url=https://tailknot1.webgarden.at]xbody[/url]
CYBER ATTACKS ON ELECTION PROCESS – Pentesting.id
Greetings! Very helpful advice in this particular
article! It is the little changes that will make the greatest changes.
Thanks a lot for sharing!
CYBER ATTACKS ON ELECTION PROCESS – Pentesting.id
Hello, I enjoy reading through your post. I like to write a little comment to support you.
You are my intake, I possess few blogs and often run out from to brand.