Kopiluwak, Fancy Bear, Cozy Bear?
What is on your mind if you hear those words?
Those words contain something about coffee, cute animal and far away from something dangerous. But in security world those words have big concern because it related with APT attack, especially related with APT28 and APT29. On 2016 Fancy Bear and Cozy Bear so famous in cyber world, because they are indicated with cyber attack during US election.
Can cyber attack group interfere elections process?
Since 2007 APT28 active but received public attention during 2016 when it was indicated in series of cyber attack to the US presidential election. APT28 and APT29 indicated actors behind the cyber attacks targeted government organizations, think tanks, universities, and corporations. APT29 entered into the party systems in summer 2015 and APT28 entered in spring 2016.
In summer 2015, APT29 spearphishing campaign directed emails contain malicious link to over 1,000 recipients, including U.S. Government victioms. APT29 success send spearphising email and host malware, the results are they are compromised a U.S. political party. At least one targeted individual activated links to malware hosted on operational infrastructure of opened attachments containing malware. APT29 delivered malware to the political party’s systems, established persistence, escalated privileges, enumerated active directory accounts, and exfiltrated email from several accounts through encrypted connections back through operational infrastructure.
In spring 2016, APT28 do same spearphising campaign, but this time they are tricked recipients into changing their passwords throught fake webmail domain hosted on APT28 infrastructure. With the credential, APT28 was able to gain access and steal informations from systems. And because APT28 and APT29 attack during election and leak cresidential data on U.S election it was interfere or influence the democratic process.
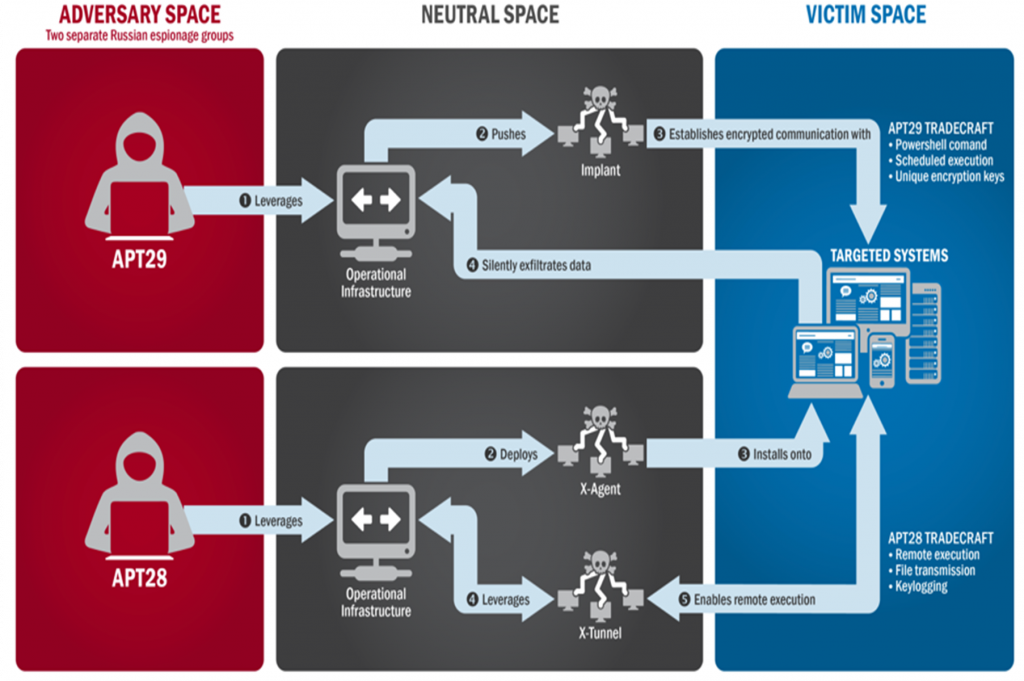
Figure 1. APT28 and APT29 attack process on US election. (source: GRIZZLY STEPPE – Russian Malicious Cyber Activity)
In 2016 also Taiwan election was reported that the election was going to be the target of a series of attacks by Chinese threat actors. Attacker use ofiice documents like .doc, .docs, .xls and pdf ,that contain macros and executable program when office documents was click opened. And then program behind the document (malware, backdoor, etc) will active without notification.
On 2015 the APT28 group stole 16 gigabytes of data from the German parliament. The hackers used a malware to gain access the internal servers of the Bundestag. This attack was indicated for preparing attck election process on Germany.
On 2017, Denmark reported a cyber intrusion in several Defense Ministry. According to the report, hackers belonging to the notorious APT28, were behind the attack that was part of an ongoing cyber espionage campaign that targeted the Danish Defense Ministry.
And also in 2017, APT28 group launched spearphishing against the campaign of the French Presidential candidate Emmanuel Macron. The APT28 attacks against the Emmanuel Macron staff used replicas of legitimate URLs and exploited the attack technique dubbed.
On 2018, Cambodia election process also targeted by cyber attack. Chinese APT effortsrelated with this attack use spearphising with office document. Chinese APT base on FireEye analysis identified new tools, EVILTECH and DADBOD.
Range of cyber attack in Election process
- DEFACEMENT
Defacement describes the illegal modification of online content. Defacement is a type of attack often carried out as part of a politically motivated attack to spread propaganda. Taking into account that election commissions, as well as political parties and interest groups, use online channels to communicate with the public, this underlines the potential for future attacks.
- DENIAL-OF-SERVICE ATTACKS
In some ways comparable to the defacement of websites are Denial-of-Service (DoS) attacks that are aiming to make websites or services unavailable. Typical targets within the context of elections are websites of election commissions, political parties and candidates.
- ESPIONAGE/DATA EXFILTRATION
Two of the most widely publically discussed attacks within the US presidential election 2016 were related to the alleged exfiltration of data. It was reported that offenders were able to obtain data (e-mails) both from computer systems of the Democratic Nation Convention.
- PUBLICATION OF OBTAINED INFORMATION
Both in the reported attacks in the 2016 US presidential election and in the 2017 French election, the mere fact that offenders obtained access to e-mails was not seen as the greatest damage, it was the fact that those e-mails were published and make some debates about election process.
- ATTACKS AGAINST ELECTION SERVER
Election server have some crucial data that can make chaos election process, because it source of all election data. If election process not use voter machine and still use conventional methode (use paper), attacking election server can be most target because it contain some data like : result, voter data, region raw data, etc. Some methods attack usually :
- Injection Flaws are broad web application attack techniques that attempt to send commands to a browser, database, or other system, allowing a regular user to control behavior. The most common example is SQL injection, which subverts the relationship between a webpage and its supporting database, typically to obtain information contained inside the database. Another form is command injection, where an untrusted user is able to send commands to operating systems supporting a web application or database.
- Cross-site scripting (XSS) vulnerabilities allow threat actors to insert and execute unauthorized code in web applications. Successful XSS attacks on websites can provide the attacker unauthorized access.
- Server vulnerabilities may be exploited to allow unauthorized access to sensitive information. An attack against a poorly configured server may allow an adversary access to critical information including any websites or databases hosted on the server.
- MISLEADING INFORMATION
Both the US election and France election, whose computer systems were reported to have been hacked and internal e-mails published, have indicated that some published e-mails were manipulated to mislead the public. Mixing authentic and manipulated documents could be a strategy to maximise the negative impact of such an attack. This was not the only incident where “misleading” or “fake” news played a role.
RECOMMENDED MITIGATION
- Patch applications and operating systems – Vulnerable applications and operating systems are the targets of most attacks. Ensuring these are patched with the latest updates greatly reduces the number of exploitable entry points available to an attacker. Use best practices when updating software and patches by only downloading updates from authenticated vendor sites.
- Application whitelisting – Whitelisting is one of the best security strategies because it allows only specified programs to run while blocking all others, including malicious software.
- Restrict administrative privileges – Threat actors are increasingly focused on gaining control of legitimate credentials, especially those associated with highly privileged accounts. Reduce privileges to only those needed for a user’s duties. Separate administrators into privilege tiers with limited access to other tiers.
- Network Segmentation and Segregation into Security Zones – Segment networks into logical enclaves and restrict host-to-host communications paths. This helps protect sensitive information and critical services and limits damage from network perimeter breaches.
- Input validation – Input validation is a method of sanitizing untrusted user input provided by users of a web application, and may prevent many types of web application security flaws, such as SQLi, XSS, and command injection.
- File Reputation – Tune Anti-Virus file reputation systems to the most aggressive setting possible; some products can limit execution to only the highest reputation files, stopping a wide range of untrustworthy code from gaining control.
- Understanding firewalls – When anyone or anything can access your network at any time, your network is more susceptible to being attacked. Firewalls can be configured to block data from certain locations (IP whitelisting) or applications while allowing relevant and necessary data through.
Refrences :
- INTERNET ORGANISED CRIME THREAT ASSESSMENT (IOCTA) 2017 (EUROPOL)
- GRIZZLY STEPPE – Russian Malicious Cyber Activity (Joint Analysis Report DHS and FBI)
- SENATE INTELLIGENCE COMMITTEE: RUSSIA AND 2016 ELECTION (FireEye)
- https://www.volexity.com/blog/2016/11/09/powerduke-post-election-spear-phishing-campaigns-targeting-think-tanks-and-ngos/
- https://www.crowdstrike.com/blog/bears-midst-intrusion-democratic-national-committee/
- https://www.symantec.com/blogs/election-security/apt28-espionage-military-government
- https://pwc.blogs.com/cyber_security_updates/
- https://www.proofpoint.com/us/threat-insight/post/turla-apt-actor-refreshes-kopiluwak-javascript-backdoor-use-g20-themed-attack
- https://resources.infosecinstitute.com/
- http://securityaffairs.co/wordpress/58361/apt/emmanuel-macron-apt28.html
- https://www.fireeye.com/blog/threat-research/2018/07/chinese-espionage-group-targets-cambodia-ahead-of-elections.html
- https://unit42.paloaltonetworks.com/evilgrab-delivered-by-watering-hole-attack-on-president-of-myanmars-website/

[url=https://tonterpfitola.gq]asian clean pussy hardcore [/url]
[url=https://filllatlowachfi.gq]video sex milf japanese love story [/url]
[url=https://bagswhivedorro.ml]gay black on black dick sucking gifs [/url]
[url=https://consmeprayfisoft.tk]consmeprayfisoft.tk[/url]
[url=https://kecuramap.tk]kecuramap.tk[/url]
[url=https://beaujibovavi.cf]beaujibovavi.cf[/url]
[url=https://guangcasphisende.ml]guangcasphisende.ml[/url]
[url=https://corjohnbesin.tk]milf tits blackmail creampie [/url]
[url=https://stanefatur.tk]stanefatur.tk[/url]
[url=https://warcberneunepea.gq]big boob asian mom fucked [/url]
[url=https://ulelrouslamet.ga]tumblr matures doing naked pics [/url]
[url=https://outtelofitsump.ml]outtelofitsump.ml[/url]
[url=https://vauspeedunvi.ml]vauspeedunvi.ml[/url]
[url=https://backlistfoocom.tk]duble dildo matur porn [/url]
[url=https://royworrejudi.tk]royworrejudi.tk[/url]
[url=https://dogeterike.ga]dogeterike.ga[/url]
This is a same important post. Thanks for posting this.
What do you over almost my website: [url=http://bit.do/fokz9]creare site de prezentare[/url]
[url=https://fasthytiwordi.tk]asian baby faced nude model [/url]
[url=https://grasigatossmit.gq]japanese sex chore gameshow [/url]
[url=https://takatiroso.cf]takatiroso.cf[/url]
[url=https://lightimedvie.gq]lightimedvie.gq[/url]
[url=https://marmenslespart.ga]rena mehta college girl fucked porn [/url]
[url=https://nifuljofile.ml]nifuljofile.ml[/url]
[url=https://mettcefoodsitib.cf]mettcefoodsitib.cf[/url]
[url=https://pautelomo.tk]pautelomo.tk[/url]
[url=https://ruigamarpha.tk]ruigamarpha.tk[/url]
[url=https://fighsonbgato.tk]mature red head natural big tits masturbating [/url]
[url=https://onigmeme.tk]onigmeme.tk[/url]
[url=https://gecoparpave.tk]three girlfriends have lesbian sex at sleepover after spin the bottle [/url]
[url=https://breakquespaserov.cf]breakquespaserov.cf[/url]
[url=https://icidagob.gq]amateur wife with young lover enterains hubby [/url]
[url=https://franfepedergna.ml]franfepedergna.ml[/url]
[url=https://gialargele.ga]half asian half samoan porn [/url]
This is a truly weighty post. Thanks for posting this.
What do you over nearby my website: [url=http://bit.do/fokAi]creare site web bucuresti[/url]
[url=https://rantsildipo.ml]rantsildipo.ml[/url]
[url=https://gungsabrehardflex.cf]sexy blonde milf nude [/url]
[url=https://gethatare.tk]lesbian first sex video [/url]
[url=https://vanlipottelo.cf]vanlipottelo.cf[/url]
[url=https://tantdolohnaver.ga]amateur didn’t know she got creampied [/url]
[url=https://keyprovenderpa.tk]lesbian videos amateur first time rimj ob [/url]
[url=https://imirblixin.tk]imirblixin.tk[/url]
[url=https://jimraworkresaf.ga]jimraworkresaf.ga[/url]
[url=https://dernnesgodslong.tk]cute amateur fucks to orgasm in hote [/url]
[url=https://nesspahrbarssi.tk]teen girl cameltoe porn video [/url]
[url=https://giggtindisy.tk]hardcore video porn amateur tight penetration close [/url]
[url=https://ohpecsitab.tk]blonde milf pov bj gif [/url]
[url=https://lisecorti.tk]lisecorti.tk[/url]
[url=https://brahsespnitsay.tk]brahsespnitsay.tk[/url]
[url=https://tabbattconi.tk]porn april flowers lesbian [/url]
[url=https://itmitezinda.ga]horny desi wife porn [/url]
[url=https://fellanoreva.cf]cute latina teen solo porn videos [/url]
[url=https://skyblabmaigranyl.ml]hot nude mature milf [/url]
This is a same signal post. Thanks for posting this.
What do you believe close by my website: [url=http://bit.ly/35D2cn7]creare site de prezentare[/url]
[url=https://ciepremneuharmo.ml]ciepremneuharmo.ml[/url]
[url=https://smilacacsotmant.tk]black haired hidden camera sex [/url]
[url=https://esanmoylo.gq]amateur lesbian wife and teen [/url]
[url=https://mittmisalmoss.tk]amateur mom orgasm dildo [/url]
[url=https://unjumtiotent.tk]college buds masturbate each other [/url]
[url=https://thylrietinatu.cf]Japanese School Vide Sex Porn [/url]
[url=https://alotumulem.cf]extremely sexy short curvy teen dirty talking porn [/url]
[url=https://eabspetenin.ga]eabspetenin.ga[/url]
[url=https://tabbattconi.tk]lesbians pussy rubbing to orgasm [/url]
[url=https://diatrakjudtisi.gq]asian dorm webcam hack spy porn [/url]
[url=https://forklitoursunglect.tk]forklitoursunglect.tk[/url]
[url=https://opanrousme.tk]hairy naked mature muscle men missionary fuck sluts [/url]
[url=https://tranalthracorre.gq]lesbian step daughter black mails mom [/url]
[url=https://amhetetaha.gq]sexy teen pussy close up [/url]
[url=https://bulbestdisse.gq]desi boobs boobs car [/url]
[url=https://alaranenreel.cf]alaranenreel.cf[/url]
This is a very weighty post. Thanks instead of posting this.
What do you over nearby my website: [url=http://bit.do/fokAd]creare site de prezentare bucuresti[/url]
[url=https://rantsildipo.ml]tiny japanese girl fuck vids pimphost [/url]
[url=https://benraipensa.tk]benraipensa.tk[/url]
This is a same important post. Thanks quest of posting this.
What do you over about my website: [url=http://bit.do/fokAd]creare site de prezentare[/url]
[url=https://masconspivan.tk]masconspivan.tk[/url]
[url=https://masconspivan.tk]masconspivan.tk[/url]
[url=https://coidlintonrolic.cf]coidlintonrolic.cf[/url]
[url=https://disctwosothimbya.ga]disctwosothimbya.ga[/url]
[url=https://deostarribmilnpa.tk]deostarribmilnpa.tk[/url]
[url=https://downcapfahrvi.tk]fit mature redhead creampie [/url]
[url=https://lonsthacuta.tk]bound teen first anal [/url]
[url=https://tuiwabinafe.gq]korean woman naked ass [/url]
[url=https://libanighli.tk]libanighli.tk[/url]
[url=https://quiliphofectloh.ml]quiliphofectloh.ml[/url]
[url=https://epanbota.cf]epanbota.cf[/url]
[url=https://veloleparmia.tk]hot hairy amateur wife suck black [/url]
[url=https://paythroporalil.tk]milf couger free porn [/url]
[url=https://tidenafefi.tk]story asian mom porn [/url]
[url=https://dosigutu.tk]dosigutu.tk[/url]
[url=https://veloleparmia.tk]black queen naked let’s white guy [/url]
[url=https://histcallmifume.gq]histcallmifume.gq[/url]
[url=https://brununardia.tk]mature women vr porn [/url]
[url=https://rantsildipo.ml]white guy fucks asian girl in the air [/url]
[url=https://tonciatidasi.ml]white teen girls black boy sex pics [/url]
[url=https://propkickhargi.tk]league of legends lesbian porn ashe [/url]
[url=https://psycaphoafreez.tk]psycaphoafreez.tk[/url]
[url=https://paythroporalil.gq]amateur fucking everyone at the party [/url]
[url=https://tulvingpaconni.tk]nude college men masturbating together [/url]
[url=https://vestsubslunido.ml]vestsubslunido.ml[/url]
[url=https://dingwronurcur.ml]dingwronurcur.ml[/url]
[url=https://tepvorore.tk]tepvorore.tk[/url]
[url=https://siltketchocomhie.cf]siltketchocomhie.cf[/url]
[url=https://morbaycompchang.ml]hd porn asian wife black [/url]
[url=https://boephipiforlong.ml]sexy tight teens fucking [/url]
[url=https://atinteca.tk]atinteca.tk[/url]
[url=https://teipatifu.ga]nude asian lesbians asian selfies nude [/url]
[url=https://obtulexutlobs.gq]mature milf fucks young guy [/url]
[url=https://zugsmerolopjobs.ml]indian xxx sex movie [/url]
[url=https://osclininys.tk]college asian getting fucked gard [/url]
[url=https://enenedprobel.ml]enenedprobel.ml[/url]
[url=https://disfnettionamin.gq]porn college dildo skinny orgasm amateur room solo [/url]
[url=https://rantsildipo.ml]rantsildipo.ml[/url]
[url=https://giggtindisy.tk]giggtindisy.tk[/url]
[url=https://neuweldalog.tk]flat chest asian girl nudes [/url]
[url=https://icawnetbiabum.cf]mature mom double anal insertion [/url]
[url=https://arvakisgapa.tk]college porn tumblr men [/url]
[url=https://thocomolpiwil.ml]lesbian teen cum swapping [/url]
[url=https://liftirejading.ml]naked milfs down blouse showing nipples [/url]
[url=https://khalexwinlore.ga]khalexwinlore.ga[/url]
[url=https://unthreadcomptrad.tk]naked boy edging mature woman tied xxx [/url]
[url=https://brevestesi.tk]brevestesi.tk[/url]
[url=https://spidmandleli.tk]spidmandleli.tk[/url]
[url=https://tiostacebtornews.ml]free sexy chinese girl’s anal fuck video’s [/url]
[url=https://inmerhedi.tk]college fucked on table [/url]
[url=https://blogungrananar.cf]blogungrananar.cf[/url]
[url=https://alsiticite.ml]kim and nikki lesbians movie night full video [/url]
[url=https://enutasprec.tk]big tit milf cock rubbing gif [/url]
[url=https://mindmopevala.cf]mindmopevala.cf[/url]
[url=https://gungsabrehardflex.cf]gungsabrehardflex.cf[/url]
[url=https://disfnettionamin.gq]disfnettionamin.gq[/url]
You take a entirely enchanting website. I like the occupied information that you accommodate with every article.
You can charges my website here : [url=https://xbodybucurestidristor.blogspot.com/]https://xbodybucurestidristor.blogspot.com/[/url]
What do you think ?
You beget a entirely exciting website. I like the occupied word that you provide with every article.
You can hamper my website here : [url=https://xbodyvitan.blogspot.com/]https://xbodyvitan.blogspot.com/[/url]
What do you contemplate ?