Kopiluwak, Fancy Bear, Cozy Bear?
What is on your mind if you hear those words?
Those words contain something about coffee, cute animal and far away from something dangerous. But in security world those words have big concern because it related with APT attack, especially related with APT28 and APT29. On 2016 Fancy Bear and Cozy Bear so famous in cyber world, because they are indicated with cyber attack during US election.
Can cyber attack group interfere elections process?
Since 2007 APT28 active but received public attention during 2016 when it was indicated in series of cyber attack to the US presidential election. APT28 and APT29 indicated actors behind the cyber attacks targeted government organizations, think tanks, universities, and corporations. APT29 entered into the party systems in summer 2015 and APT28 entered in spring 2016.
In summer 2015, APT29 spearphishing campaign directed emails contain malicious link to over 1,000 recipients, including U.S. Government victioms. APT29 success send spearphising email and host malware, the results are they are compromised a U.S. political party. At least one targeted individual activated links to malware hosted on operational infrastructure of opened attachments containing malware. APT29 delivered malware to the political party’s systems, established persistence, escalated privileges, enumerated active directory accounts, and exfiltrated email from several accounts through encrypted connections back through operational infrastructure.
In spring 2016, APT28 do same spearphising campaign, but this time they are tricked recipients into changing their passwords throught fake webmail domain hosted on APT28 infrastructure. With the credential, APT28 was able to gain access and steal informations from systems. And because APT28 and APT29 attack during election and leak cresidential data on U.S election it was interfere or influence the democratic process.
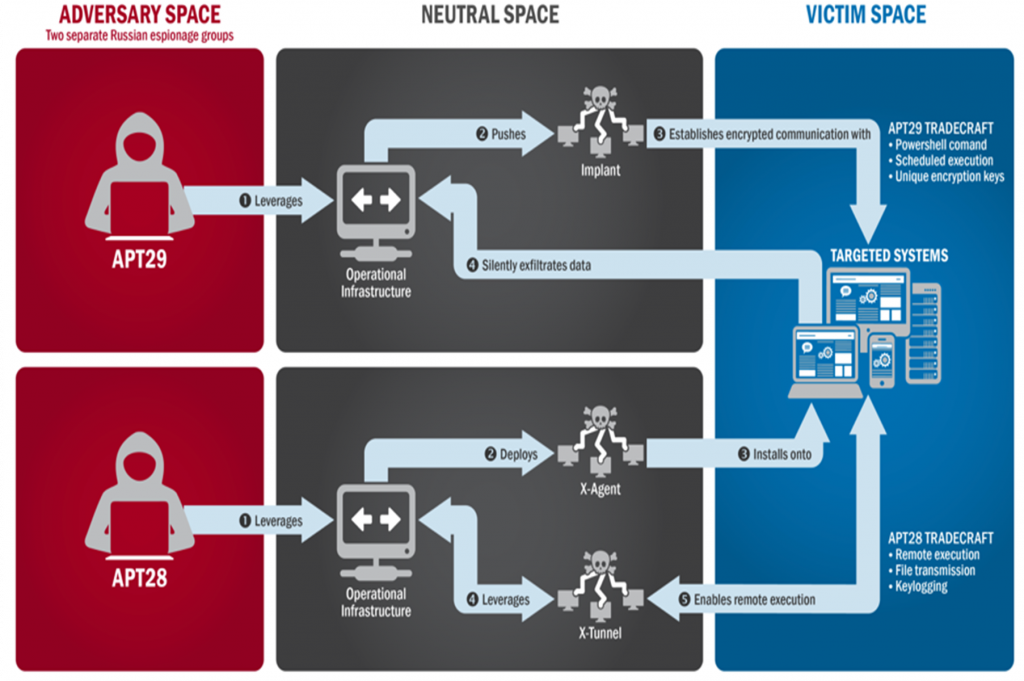
Figure 1. APT28 and APT29 attack process on US election. (source: GRIZZLY STEPPE – Russian Malicious Cyber Activity)
In 2016 also Taiwan election was reported that the election was going to be the target of a series of attacks by Chinese threat actors. Attacker use ofiice documents like .doc, .docs, .xls and pdf ,that contain macros and executable program when office documents was click opened. And then program behind the document (malware, backdoor, etc) will active without notification.
On 2015 the APT28 group stole 16 gigabytes of data from the German parliament. The hackers used a malware to gain access the internal servers of the Bundestag. This attack was indicated for preparing attck election process on Germany.
On 2017, Denmark reported a cyber intrusion in several Defense Ministry. According to the report, hackers belonging to the notorious APT28, were behind the attack that was part of an ongoing cyber espionage campaign that targeted the Danish Defense Ministry.
And also in 2017, APT28 group launched spearphishing against the campaign of the French Presidential candidate Emmanuel Macron. The APT28 attacks against the Emmanuel Macron staff used replicas of legitimate URLs and exploited the attack technique dubbed.
On 2018, Cambodia election process also targeted by cyber attack. Chinese APT effortsrelated with this attack use spearphising with office document. Chinese APT base on FireEye analysis identified new tools, EVILTECH and DADBOD.
Range of cyber attack in Election process
- DEFACEMENT
Defacement describes the illegal modification of online content. Defacement is a type of attack often carried out as part of a politically motivated attack to spread propaganda. Taking into account that election commissions, as well as political parties and interest groups, use online channels to communicate with the public, this underlines the potential for future attacks.
- DENIAL-OF-SERVICE ATTACKS
In some ways comparable to the defacement of websites are Denial-of-Service (DoS) attacks that are aiming to make websites or services unavailable. Typical targets within the context of elections are websites of election commissions, political parties and candidates.
- ESPIONAGE/DATA EXFILTRATION
Two of the most widely publically discussed attacks within the US presidential election 2016 were related to the alleged exfiltration of data. It was reported that offenders were able to obtain data (e-mails) both from computer systems of the Democratic Nation Convention.
- PUBLICATION OF OBTAINED INFORMATION
Both in the reported attacks in the 2016 US presidential election and in the 2017 French election, the mere fact that offenders obtained access to e-mails was not seen as the greatest damage, it was the fact that those e-mails were published and make some debates about election process.
- ATTACKS AGAINST ELECTION SERVER
Election server have some crucial data that can make chaos election process, because it source of all election data. If election process not use voter machine and still use conventional methode (use paper), attacking election server can be most target because it contain some data like : result, voter data, region raw data, etc. Some methods attack usually :
- Injection Flaws are broad web application attack techniques that attempt to send commands to a browser, database, or other system, allowing a regular user to control behavior. The most common example is SQL injection, which subverts the relationship between a webpage and its supporting database, typically to obtain information contained inside the database. Another form is command injection, where an untrusted user is able to send commands to operating systems supporting a web application or database.
- Cross-site scripting (XSS) vulnerabilities allow threat actors to insert and execute unauthorized code in web applications. Successful XSS attacks on websites can provide the attacker unauthorized access.
- Server vulnerabilities may be exploited to allow unauthorized access to sensitive information. An attack against a poorly configured server may allow an adversary access to critical information including any websites or databases hosted on the server.
- MISLEADING INFORMATION
Both the US election and France election, whose computer systems were reported to have been hacked and internal e-mails published, have indicated that some published e-mails were manipulated to mislead the public. Mixing authentic and manipulated documents could be a strategy to maximise the negative impact of such an attack. This was not the only incident where “misleading” or “fake” news played a role.
RECOMMENDED MITIGATION
- Patch applications and operating systems – Vulnerable applications and operating systems are the targets of most attacks. Ensuring these are patched with the latest updates greatly reduces the number of exploitable entry points available to an attacker. Use best practices when updating software and patches by only downloading updates from authenticated vendor sites.
- Application whitelisting – Whitelisting is one of the best security strategies because it allows only specified programs to run while blocking all others, including malicious software.
- Restrict administrative privileges – Threat actors are increasingly focused on gaining control of legitimate credentials, especially those associated with highly privileged accounts. Reduce privileges to only those needed for a user’s duties. Separate administrators into privilege tiers with limited access to other tiers.
- Network Segmentation and Segregation into Security Zones – Segment networks into logical enclaves and restrict host-to-host communications paths. This helps protect sensitive information and critical services and limits damage from network perimeter breaches.
- Input validation – Input validation is a method of sanitizing untrusted user input provided by users of a web application, and may prevent many types of web application security flaws, such as SQLi, XSS, and command injection.
- File Reputation – Tune Anti-Virus file reputation systems to the most aggressive setting possible; some products can limit execution to only the highest reputation files, stopping a wide range of untrustworthy code from gaining control.
- Understanding firewalls – When anyone or anything can access your network at any time, your network is more susceptible to being attacked. Firewalls can be configured to block data from certain locations (IP whitelisting) or applications while allowing relevant and necessary data through.
Refrences :
- INTERNET ORGANISED CRIME THREAT ASSESSMENT (IOCTA) 2017 (EUROPOL)
- GRIZZLY STEPPE – Russian Malicious Cyber Activity (Joint Analysis Report DHS and FBI)
- SENATE INTELLIGENCE COMMITTEE: RUSSIA AND 2016 ELECTION (FireEye)
- https://www.volexity.com/blog/2016/11/09/powerduke-post-election-spear-phishing-campaigns-targeting-think-tanks-and-ngos/
- https://www.crowdstrike.com/blog/bears-midst-intrusion-democratic-national-committee/
- https://www.symantec.com/blogs/election-security/apt28-espionage-military-government
- https://pwc.blogs.com/cyber_security_updates/
- https://www.proofpoint.com/us/threat-insight/post/turla-apt-actor-refreshes-kopiluwak-javascript-backdoor-use-g20-themed-attack
- https://resources.infosecinstitute.com/
- http://securityaffairs.co/wordpress/58361/apt/emmanuel-macron-apt28.html
- https://www.fireeye.com/blog/threat-research/2018/07/chinese-espionage-group-targets-cambodia-ahead-of-elections.html
- https://unit42.paloaltonetworks.com/evilgrab-delivered-by-watering-hole-attack-on-president-of-myanmars-website/

Thanks a lot for giving everyone remarkably superb chance to discover important secrets from this website. It really is very superb and also full of amusement for me and my office acquaintances to search your blog at a minimum three times in one week to see the latest issues you will have. And definitely, I’m also at all times pleased with the fantastic concepts you serve. Some 1 tips in this posting are undeniably the most suitable we have had.
CYBER ATTACKS ON ELECTION PROCESS – Pentesting.id http://5-55.xn--p1ai/bitrix/redirect.php?event1=&event2=&event3=&goto=https://www.hongkongpool.io/
I must show my respect for your generosity supporting all those that actually need help with that concern. Your personal commitment to passing the message all over came to be remarkably functional and has really helped women like me to get to their objectives. This valuable tutorial means much to me and further more to my office colleagues. Best wishes; from everyone of us.
CYBER ATTACKS ON ELECTION PROCESS – Pentesting.id
Very agreeably article . I couldn’t coincide more on the report provided.
What do you deem thither my locate ? [url=https://mortengade.dk/2010/mine-seneste-bookmarks-17-04-10-03-05-10/?share=facebook]mineral makeup set[/url]
CYBER ATTACKS ON ELECTION PROCESS – Pentesting.id http://atletika.ru/bitrix/redirect.php?event1=&event2=&event3=&goto=http://18.182.187.26/
CYBER ATTACKS ON ELECTION PROCESS – Pentesting.id http://banner.ntop.tv/click.php?a=237&z=59&c=1&url=http://18.182.187.26/
CYBER ATTACKS ON ELECTION PROCESS – Pentesting.id http://autos.car1.hk/external.php?url=http%3A%2F%2F18.182.187.26%2F
CYBER ATTACKS ON ELECTION PROCESS – Pentesting.id http://app.anda.jor.br/ex/l/MjU5Njg=/OTY0ODU=/NDU3NDkxMzQ=/?addr=http://18.182.187.26/
CYBER ATTACKS ON ELECTION PROCESS – Pentesting.id http://chiswickw4.com/default.asp?section=info&link=http://18.182.187.26/
CYBER ATTACKS ON ELECTION PROCESS – Pentesting.id http://biriy-portal.info/rank.php?mode=link&id=492&url=http://18.182.187.26/
CYBER ATTACKS ON ELECTION PROCESS – Pentesting.id http://annyaurora19.com/wp-content/plugins/AND-AntiBounce/redirector.php?url=http://18.182.187.26/
CYBER ATTACKS ON ELECTION PROCESS – Pentesting.id http://americanheritage-realtors.com/SearchPoint/redir.asp?reg_id=pTypes&sname=/searchpoint/search.asp&lid=0&sponsor=INC&url=http://18.182.187.26/
CYBER ATTACKS ON ELECTION PROCESS – Pentesting.id http://bannery.ccb.cz/inc/redirect.php?id=3150&kam=http://18.182.187.26/
CYBER ATTACKS ON ELECTION PROCESS – Pentesting.id http://chiase123.com/redirect.php?http://18.182.187.26/
CYBER ATTACKS ON ELECTION PROCESS – Pentesting.id http://belovo-spshka.com/go.php?http://18.182.187.26/
CYBER ATTACKS ON ELECTION PROCESS – Pentesting.id http://cat29.ru/bitrix/redirect.php?event1=&event2=&event3=&goto=http://18.182.187.26/
CYBER ATTACKS ON ELECTION PROCESS – Pentesting.id http://neoclassica-asc.com/links/rank.php?url=http://18.182.187.26/
CYBER ATTACKS ON ELECTION PROCESS – Pentesting.id http://hairy-top.com/cgi-bin/out.cgi?id=hairytop&url=https://www.hongkongpool.io/
Servicios prestados: Venta directa de electrodomésticos al mejor precio, reparación de frigorífico, instalación de horno, reparación de aire acondicionado, reparación de secadora, instalación de Vitrocerámica, reparación de lavadora, reparación nevera, reparación de nevera, reparar nevera, instalación de lavavajillas, reparar frigorífico, instalar lavadora, reparar frigo, instalar horno, reparar lavadora, instalar Vitrocerámica, reparación de vítro, instalación de lavadora, reparar vitro, instalar lavavajillas, instalación de secadora, instalar secadora, reparación de frigo, instalación de secadora, reparar secadora, reparación SAT, SAT electrodomésticos, técnico de electrodomésticos, venta de frigoríficos lavadoras, lavavajillas, secadoras, hornos, Vitrocerámica, campanas, etc. Nuestro servicio de Urgencias, no tiene coste adicional, de tal manera que junto con nuestro DESPLAZAMIENTO GRATUITO si repara, hará que su lavadora Edesa, vuelva a funcionar como el primer día al mejor precio posible en Madrid. Nuestro equipo técnico posee conocimientos actualizados y experiencia, garantizados por una amplia formación técnica y de producto, así como cursos de actualización.