Kopiluwak, Fancy Bear, Cozy Bear?
What is on your mind if you hear those words?
Those words contain something about coffee, cute animal and far away from something dangerous. But in security world those words have big concern because it related with APT attack, especially related with APT28 and APT29. On 2016 Fancy Bear and Cozy Bear so famous in cyber world, because they are indicated with cyber attack during US election.
Can cyber attack group interfere elections process?
Since 2007 APT28 active but received public attention during 2016 when it was indicated in series of cyber attack to the US presidential election. APT28 and APT29 indicated actors behind the cyber attacks targeted government organizations, think tanks, universities, and corporations. APT29 entered into the party systems in summer 2015 and APT28 entered in spring 2016.
In summer 2015, APT29 spearphishing campaign directed emails contain malicious link to over 1,000 recipients, including U.S. Government victioms. APT29 success send spearphising email and host malware, the results are they are compromised a U.S. political party. At least one targeted individual activated links to malware hosted on operational infrastructure of opened attachments containing malware. APT29 delivered malware to the political party’s systems, established persistence, escalated privileges, enumerated active directory accounts, and exfiltrated email from several accounts through encrypted connections back through operational infrastructure.
In spring 2016, APT28 do same spearphising campaign, but this time they are tricked recipients into changing their passwords throught fake webmail domain hosted on APT28 infrastructure. With the credential, APT28 was able to gain access and steal informations from systems. And because APT28 and APT29 attack during election and leak cresidential data on U.S election it was interfere or influence the democratic process.
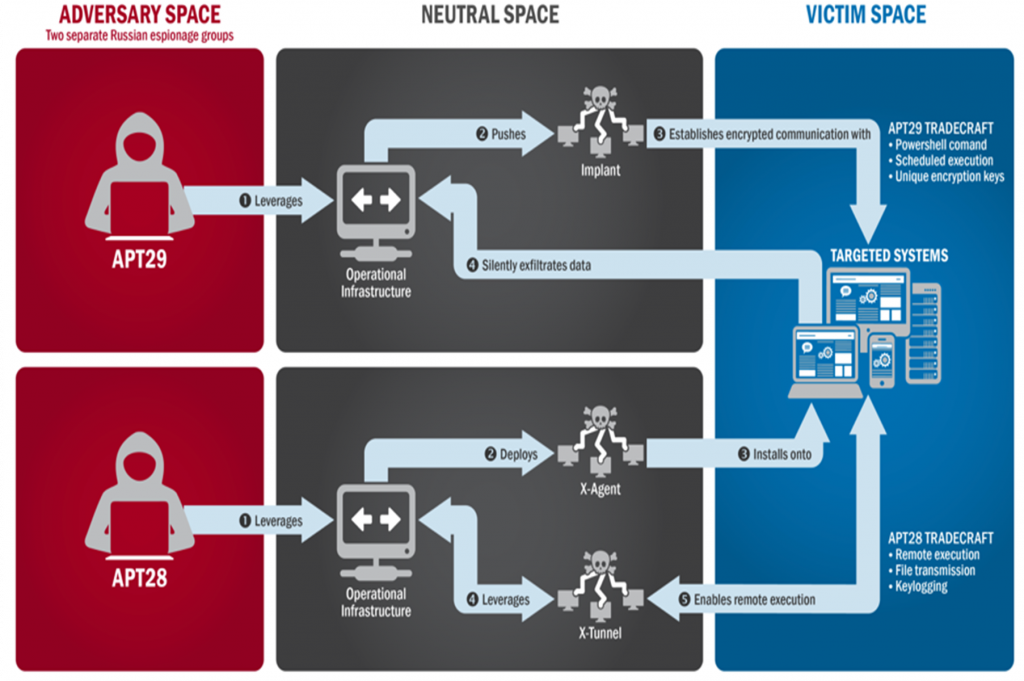
Figure 1. APT28 and APT29 attack process on US election. (source: GRIZZLY STEPPE – Russian Malicious Cyber Activity)
In 2016 also Taiwan election was reported that the election was going to be the target of a series of attacks by Chinese threat actors. Attacker use ofiice documents like .doc, .docs, .xls and pdf ,that contain macros and executable program when office documents was click opened. And then program behind the document (malware, backdoor, etc) will active without notification.
On 2015 the APT28 group stole 16 gigabytes of data from the German parliament. The hackers used a malware to gain access the internal servers of the Bundestag. This attack was indicated for preparing attck election process on Germany.
On 2017, Denmark reported a cyber intrusion in several Defense Ministry. According to the report, hackers belonging to the notorious APT28, were behind the attack that was part of an ongoing cyber espionage campaign that targeted the Danish Defense Ministry.
And also in 2017, APT28 group launched spearphishing against the campaign of the French Presidential candidate Emmanuel Macron. The APT28 attacks against the Emmanuel Macron staff used replicas of legitimate URLs and exploited the attack technique dubbed.
On 2018, Cambodia election process also targeted by cyber attack. Chinese APT effortsrelated with this attack use spearphising with office document. Chinese APT base on FireEye analysis identified new tools, EVILTECH and DADBOD.
Range of cyber attack in Election process
- DEFACEMENT
Defacement describes the illegal modification of online content. Defacement is a type of attack often carried out as part of a politically motivated attack to spread propaganda. Taking into account that election commissions, as well as political parties and interest groups, use online channels to communicate with the public, this underlines the potential for future attacks.
- DENIAL-OF-SERVICE ATTACKS
In some ways comparable to the defacement of websites are Denial-of-Service (DoS) attacks that are aiming to make websites or services unavailable. Typical targets within the context of elections are websites of election commissions, political parties and candidates.
- ESPIONAGE/DATA EXFILTRATION
Two of the most widely publically discussed attacks within the US presidential election 2016 were related to the alleged exfiltration of data. It was reported that offenders were able to obtain data (e-mails) both from computer systems of the Democratic Nation Convention.
- PUBLICATION OF OBTAINED INFORMATION
Both in the reported attacks in the 2016 US presidential election and in the 2017 French election, the mere fact that offenders obtained access to e-mails was not seen as the greatest damage, it was the fact that those e-mails were published and make some debates about election process.
- ATTACKS AGAINST ELECTION SERVER
Election server have some crucial data that can make chaos election process, because it source of all election data. If election process not use voter machine and still use conventional methode (use paper), attacking election server can be most target because it contain some data like : result, voter data, region raw data, etc. Some methods attack usually :
- Injection Flaws are broad web application attack techniques that attempt to send commands to a browser, database, or other system, allowing a regular user to control behavior. The most common example is SQL injection, which subverts the relationship between a webpage and its supporting database, typically to obtain information contained inside the database. Another form is command injection, where an untrusted user is able to send commands to operating systems supporting a web application or database.
- Cross-site scripting (XSS) vulnerabilities allow threat actors to insert and execute unauthorized code in web applications. Successful XSS attacks on websites can provide the attacker unauthorized access.
- Server vulnerabilities may be exploited to allow unauthorized access to sensitive information. An attack against a poorly configured server may allow an adversary access to critical information including any websites or databases hosted on the server.
- MISLEADING INFORMATION
Both the US election and France election, whose computer systems were reported to have been hacked and internal e-mails published, have indicated that some published e-mails were manipulated to mislead the public. Mixing authentic and manipulated documents could be a strategy to maximise the negative impact of such an attack. This was not the only incident where “misleading” or “fake” news played a role.
RECOMMENDED MITIGATION
- Patch applications and operating systems – Vulnerable applications and operating systems are the targets of most attacks. Ensuring these are patched with the latest updates greatly reduces the number of exploitable entry points available to an attacker. Use best practices when updating software and patches by only downloading updates from authenticated vendor sites.
- Application whitelisting – Whitelisting is one of the best security strategies because it allows only specified programs to run while blocking all others, including malicious software.
- Restrict administrative privileges – Threat actors are increasingly focused on gaining control of legitimate credentials, especially those associated with highly privileged accounts. Reduce privileges to only those needed for a user’s duties. Separate administrators into privilege tiers with limited access to other tiers.
- Network Segmentation and Segregation into Security Zones – Segment networks into logical enclaves and restrict host-to-host communications paths. This helps protect sensitive information and critical services and limits damage from network perimeter breaches.
- Input validation – Input validation is a method of sanitizing untrusted user input provided by users of a web application, and may prevent many types of web application security flaws, such as SQLi, XSS, and command injection.
- File Reputation – Tune Anti-Virus file reputation systems to the most aggressive setting possible; some products can limit execution to only the highest reputation files, stopping a wide range of untrustworthy code from gaining control.
- Understanding firewalls – When anyone or anything can access your network at any time, your network is more susceptible to being attacked. Firewalls can be configured to block data from certain locations (IP whitelisting) or applications while allowing relevant and necessary data through.
Refrences :
- INTERNET ORGANISED CRIME THREAT ASSESSMENT (IOCTA) 2017 (EUROPOL)
- GRIZZLY STEPPE – Russian Malicious Cyber Activity (Joint Analysis Report DHS and FBI)
- SENATE INTELLIGENCE COMMITTEE: RUSSIA AND 2016 ELECTION (FireEye)
- https://www.volexity.com/blog/2016/11/09/powerduke-post-election-spear-phishing-campaigns-targeting-think-tanks-and-ngos/
- https://www.crowdstrike.com/blog/bears-midst-intrusion-democratic-national-committee/
- https://www.symantec.com/blogs/election-security/apt28-espionage-military-government
- https://pwc.blogs.com/cyber_security_updates/
- https://www.proofpoint.com/us/threat-insight/post/turla-apt-actor-refreshes-kopiluwak-javascript-backdoor-use-g20-themed-attack
- https://resources.infosecinstitute.com/
- http://securityaffairs.co/wordpress/58361/apt/emmanuel-macron-apt28.html
- https://www.fireeye.com/blog/threat-research/2018/07/chinese-espionage-group-targets-cambodia-ahead-of-elections.html
- https://unit42.paloaltonetworks.com/evilgrab-delivered-by-watering-hole-attack-on-president-of-myanmars-website/

Al quejarme de la falta de asistencia, una mujer con una soberbia irritante me dijo que podia haber pedido un tecnico por 38 euros. Yo he solicitado la devolucion del producto, y me dicen que no. He solicitado un tecnico y me dicen que hoy no se puede. La marca envia al SAT (Servicio técnico) y reparan… pero vaya reparación!!!!!, corta y pega con celo el circuito eléctrico.
CYBER ATTACKS ON ELECTION PROCESS – Pentesting.id
Hey very nice site!! Man .. Beautiful .. Superb ..
I’ll bookmark your site and take the feeds also? I am satisfied to seek out numerous useful information here within the put up,
we need work out more strategies on this regard, thanks for sharing.
. . . . .
Más de 15 años de experiencia en el sector de la reparación de electrodomésticos nos avalan para garantizar la correcta reparación, instalación y mantenimiento de todos sus electrodomésticos de gama blanca en Madrid y solucionar todas lsa averías que sus electrodomésticos puedan presentar. La etiqueta energética de estos electrodomésticos nos indica de forma rápida y sencilla la eficiencia energética de los electrodomésticos.
Nada más verme me dijo que MAURO le había pasado mi informe sobre mi conferencia en la Universidad de HAIER y que él, a su vez, lo había remitido a la cúpula de HAIER, ya que, según me dijo, mi informe ratificaba todo lo que él no se cansaba de repetir a los chinos: la necesidad imperiosa de organizar un almacén de recambios en la fábrica, otro en Europa, y poner los medios para la implantación de una organización importante de Servicios en Europa.
It’s actually a cool and useful piece of information. I am satisfied that you simply shared this
helpful information with us. Please keep us informed like this.
Thanks for sharing.
Estamos autorizados para la realización de todo tipo de servicios que guarden relación con el gas, realizando el trabajo solucionando el problema en muy poco tiempo. Cualquier instalador profesional gas Daganzo de nuestra empresa usara siempre las técnicas menos invasivas, los mejores materiales y las herramientas de mayor calidad, lo que hará que el trabajo se pueda realizar en mucho menos tiempo, pero de una forma más eficaz y con garantía. Instalación y Reparación de: Calderas de Gas, Calderas Eléctricas, precios economicos en Daganzo para sus Calderas de Gas-Oil, Calentadores y Termos.
Normalmente las reparaciones más habituales como cambio de bomba en lavadoras, arreglos de emboces en neveras, etc se suele reparar insitu en la casa del cliente, siempre y cuando nos hayan especificado el modelo y marca del electrodoméstico, y en menos de 24 horas ya la tiene arreglada. Nuestro servicio técnico colaborador trabaja con las principales marcas de electrodomésticos, como Bosch, Siemenes, Balay, AEG, Zanushi, Fagor, Hotpoint, Samsung, LG, Otsein, etc. Si estás buscando técnicos para la reparación de lavadoras, contacta sin compromiso y hasta 4 técnicos te darán un presupuesto personalizado para saber cuanto cuesta reparar una lavadora.
Se requiere amplia experiencia en manejo de caja y en el análisis del perfil del solicitante (no excluyente) aptitud comercial para el cierre del crédito, manejo posnet, caja y moneda extranjera. Nos encontramos en la búsqueda de un Auxiliar de Repuestos para formar parte del plantel de Posventa de un Importante Concesionario Oficial FORD.
En estos tiempos de crisis en los que estamos es fundamental el ahorro, por este motivo nosotros entendemos que AHORRAR es evitar un gasto consumo mayor. Con la experiencia y solidez de más de 30 años de trabajo, nos hemos afianzado como uno de los mejores y mas reconocidos servicios de asistencia técnica de electrodomésticos.
Por poner ejemplos, un serie 3 Compact 320d de 150 CV alcanza valoraciones indignas para un coche de su fiabilidad, un Citroën SM esta sobrevaloradísimo para lo malo que salió y otros muchos coches de imagen más tierna pero muy buenos electrodomésticos no tienen una valoración acorde con sus valores objetivos. En el mercado de los clásicos, el precio de un vehículo depende de factores más importantes que la fiabilidad. Después, recorra España de Sur a Norte con cara de confort, y al llegar al final pise a fondo.
Anualmente recoge eventos tan importantes como la Cibeles Madrid Fashion Week, el mercadillo El Rastro la Feria del Libro de Madrid. Se trata de una ciudad muy grande, lo que hace que sea importante valorar las diferentes opciones de hoteles en Madrid existentes antes de decantarse por una de ellas, puesto que no todas ofrecen la misma buena relación entre calidad y precio. Somos Frío Jerez, S.L., una empresa especializada en la venta de aire acondicionado.
Recambios de aire acondicionado SAUNIER DUVAL en BarcelonaRecambios de aire acondicionado SAUNIER DUVAL en Barcelona… Recambios de Aire Acondicionado, repuestos , accesorios, filtros, termostatos,, Home. Epígrafe 113.2.- Preparación de lignito pardo en factoría independiente fuera del perímetro de la concesión explotación minera. No realizamos intervenciones en Electrodomésticos Bosch Mallorca en Garantia de Fábrica.
En Estepona ofrecemos a nuestros clientes un servicio para SIEMENS de calidad cumpliendo las más altas expectativas y ofreciendo garantía en nuestras reparaciones a sus electrodomesticos. Ofrecemos un servicio de asistencia técnica SIEMENS en Estepona para electrodomésticos, aire acondicionado y equipos de calefacción y agua sanitaria. Si usted desea solicitar un servicio urgente en Estepona, contacte con nosotros y solicítelo, en un máximo de 2 horas atenderemos su avería.
Mi consejo es el sentido común, el mismo que cuando reparamos nuestro automovil, preguntamos, buscamos un taller conocido, confiable, que nos recomienden, y comparamos precio, que lo de las marcas es muy subjetivo.
commentx7o0rego
comment
Tanto en empresas de la hosteleria como en hogares, debe ofrecerse profesionalidad en todos los ambitos de los electrodomesticos y sus posibles averias.
Lo única solución de parte de la tienda era llevarlo al servicio de reparación de VAIO que una vez me lo trajeron el problema aún persistia. Peró por el servicio telefónico no tengo ninguna queja porque se me están llevando muy bien y con mucho interés para solucionar el problema. Devuelven las máquinas rayadas y manchadas, aunque tu hagas hincapié en su cuidado.
Menaje del Hogar es una empresa que trabaja tanto en el ámbito local como provincial de la Comunidad de Autónoma de Madrid, contando con una oficina central de administración y con técnicos distribuidos en todas las zonas en las que prestan sus servicios. Estamos abiertos a nuestros clientes antes, mientras y después de hacer nuestro trabajo, de reparación Frigorificos Liebherr si tiene alguna sugerencia nuestro personal telefónico le atenderá gustosamente porque estamos deseando escucharlas. Servicio técnico Liebherr aseguramos la máxima calidad en las reparacion de Frigorificos Liebherr y los repuestos, así como en otros aspectos también importantes como la amabilidad, información honestidad y transparencia.